PKI Infrastructure and How It Works
PKI Infrastructure
I am writing this blog today after completing a long piece of work around HashiCorp Vault on my project which involved a lot of complicated work involving PKI, Root/Intermediate CA's, CA bundles and Certificates.
My reason for writing this is because prior to starting this I had 0 experience in any of this and I find it's worth the time to explain some of this in the most simplistic way possible, so lets get into it.
Some of the topics we will cover today are the following:
- PKI
- Functionality of PKI
- What is a certificate
- Certificate hierarchies and how it works
- CA Certificate chains
What is PKI?
A PKI otherwise known as (Public Key Infrastructure) is used to generate X.509 certificates. This is the one of the key components of HashiCorp Vault that allows us to generate certificates which can be used for services without having to go and do the manual process of generating a private key, CSR and then having to go and get it signed by a trusted Root CA.
The best part of this process is that there is no waiting for a verification and signing process to get completed. Vault has its own built-in authentication & authorisation mechanisms built, in which makes a more streamlined process rather than your traditional certificate process.
The “key” part of PKI
So, what about the “key” part of PKI?
PKI implements cryptography to secure communications. Cryptography is the method of protecting data and communications through codes and techniques.
- A private key that must be kept secret
- A public key that can be freely shared with anyone
Asymmetric cryptography uses a pair of keys, a public key and a private key is used to encrypt and decrypt data.
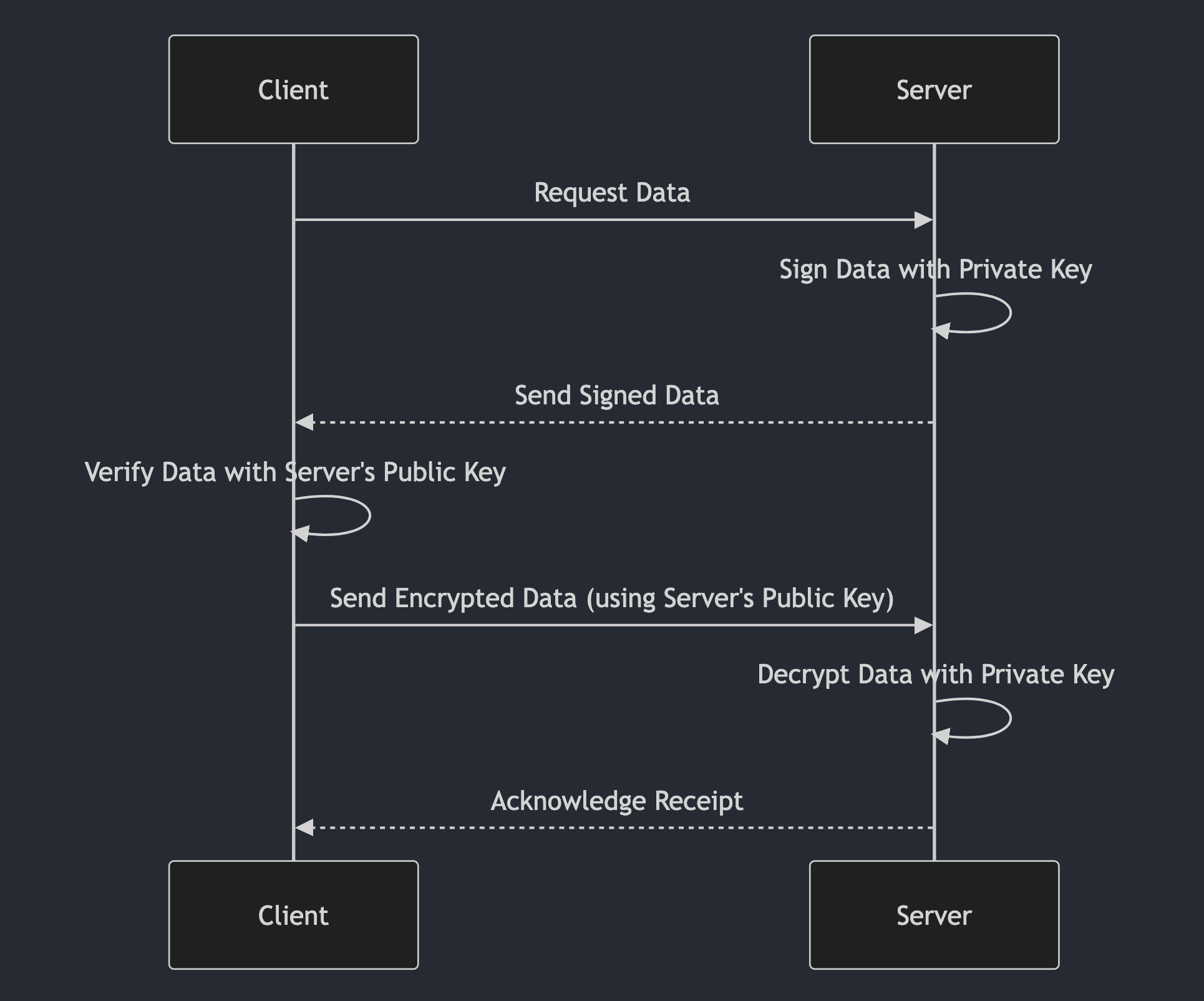
When a server sends you data using PKI:
- The server signs the data with its private key
- You can verify this signature using the server's public key
- This verification confirms the data hasn't been tampered with and genuinely comes from the server.
So what are the key functionalities of PKI?
1. Generates certificates for services to use
2. Removes the need to manually follow a standard and lengthy certificate generating process
3. Vault provides a built in authentication and authorisation mechanism
What is a certificate?
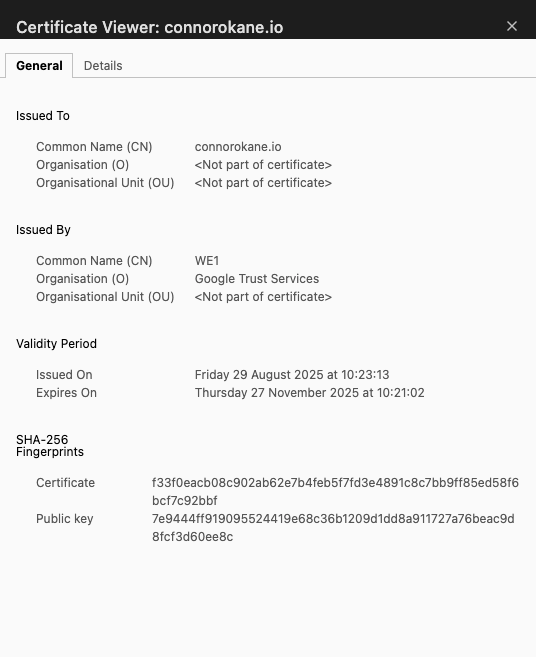
In its most simple form, a certificate is just a digital document that contains some information about whatever its representing. The information that a certificate might include is the following:
1. Subject: CN= < Name of the certificate >
2. DNS: This section will include any DNS records associated to the certificate.
3. Validity period for this certificate: This will include the date/time that the certificate is valid from - to.
4. Issuer: This will be the name of the Root CA the certificate has been signed by.
5. Certificate: This will be the serial number of the certificate.
Any server that you connect to securely, like this blog I own for example, will present you with a certificate
- You and your system must then decide if you trust that certificate.
- If you do, then you can use the public key contained within the certificate to encrypt data that only the server can decrypt.
- The server can then use its private key to sign data that you can verify with the public key contained within the certificate - https://connorokane.io
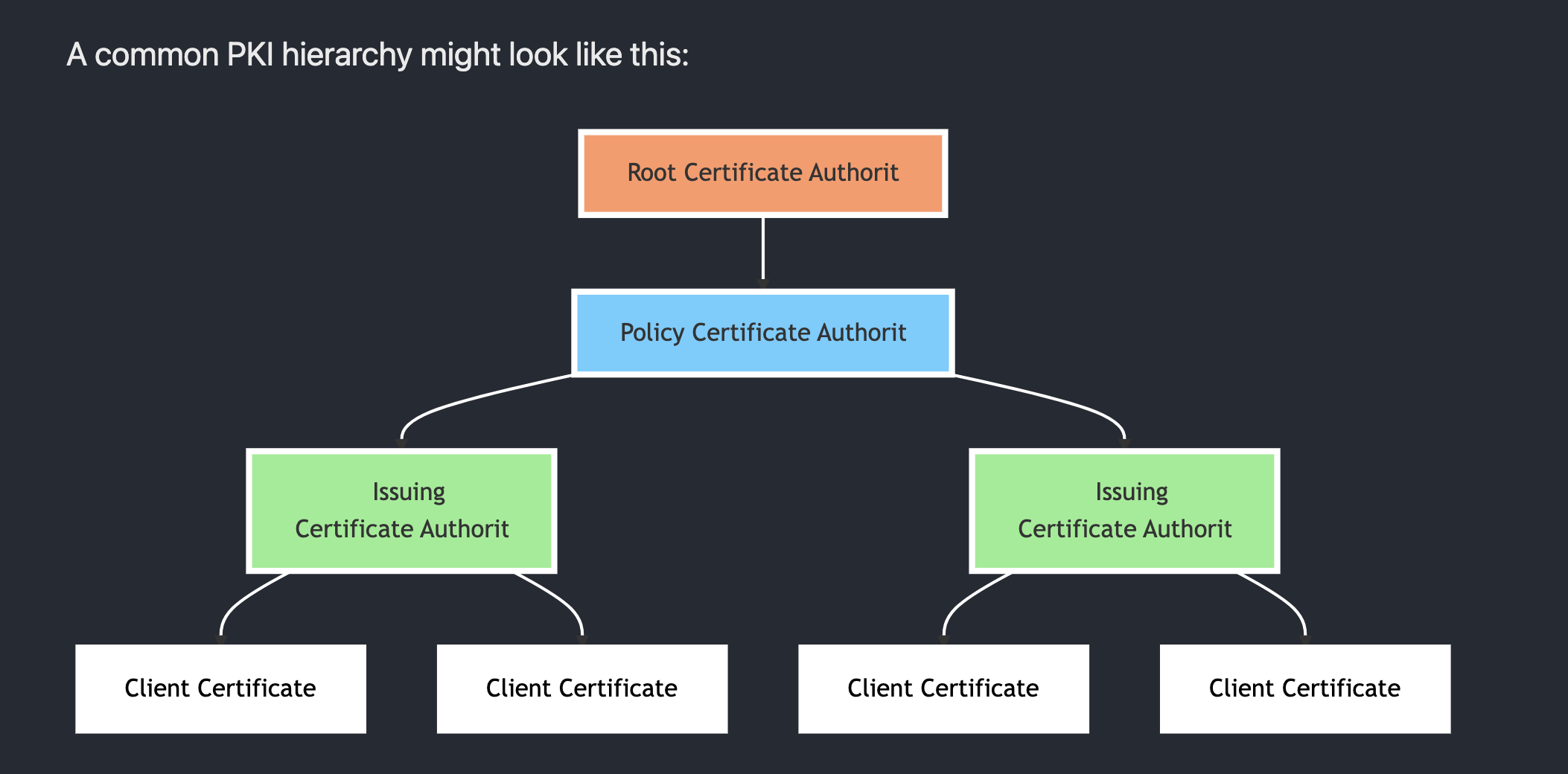
Certificate Hierarchies
A certificate hierarchy is a layered structure that establishes a chain of trust for digital certificates, beginning with a trusted Root Certificate Authority (CA) at the top.
The Root CA issues certificates to subordinate intermediate CAs, which in turn issue certificates to end entities like websites or users. This hierarchy allows for the scalable distribution of trust, enabling secure, encrypted communication by verifying the authenticity of each certificate in the chain back to the root.
How it works
Root CA:
The foundation of the trust chain. It is typically highly secured and offline to minimize the risk of compromise.
Intermediate CAs:
These Intermediate CA's are issued certificates by the Root CA. They have the authority to issue end-entity certificates and manage administrative tasks. There can be multiple levels of intermediate CA's but we can adventure into that at a later date. For now lets keep it simple.
End-Entity Certificates:
These are certificates issued to users, devices, or servers. When a browser needs to establish a secure connection, it can trace the certificate's path back through the intermediate CAs to the Root CA to verify its authenticity.
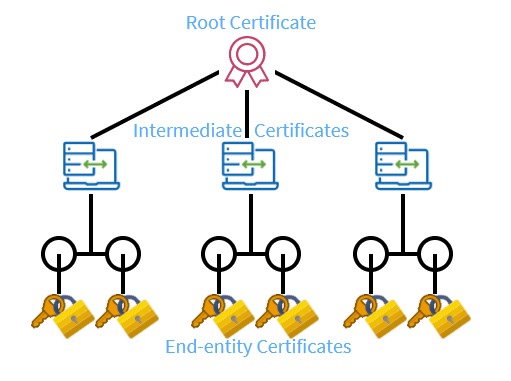
How the CA Chain works
Last but not least, lets cover what a valid CA Chain is and how it works in real life.
A CA certificate chain is used to create a chain of trust, which allows the receiver to verify that an end-entity certificate (like an SSL certificate for a website) was issued by a legitimate and trusted source. It works by linking the end certificate back through to the Intermediate certificate to a trusted Root CA.
For example when you visit this blog, it works by linking the client certificate through to the Intermediate CA which in turn then goes to the Root CA.
-
End-Entity Certificate:
The certificate you receive, such as for a website's SSL certificate, is the "end-entity" or "leaf" certificate.
-
Intermediate certificate:
This certificate is signed by an Intermediate CA. You then receive the Intermediate CA's certificate, which is the next link in the chain.
-
Root CA Certificate:
The Intermediate CA's certificate is signed by another CA, and this process continues until you reach a Root CA.
-
Verification:
The receiver's system checks the entire chain, verifying that each certificate was signed by the next one up the chain.
-
Root CA trust.
Finally, the system verifies that the top-level Root CA's certificate is a trusted root certificate stored in its own trust store.
Conclusion
The beauty of PKI lies in the simplicity beneath the complexity. It's simply about establishing trust through a hierarchical system of verification. Each certificate in the chain vouches for the next in a pattern of 3 (Root CA > Intermediate CA > SSL certs) creating an unbroken link of trust from your browser all the way to a highly secured Root CA.
Whilst PKI might seem daunting at first, with patience and the right approach, it becomes just another tool in your technical arsenal – one that's absolutely essential for securing modern infrastructure. If I can do this, then so can you!